KoPlayer
Byemwul64, December 2, 2020 in Emsisoft Anti Malware Home. Simply open the C:Windows folder. But it is not advisable to delete or disable the dwm. Then in Command Prompt, type in sfc/scannow and then hit the Enter key. If you however disable the option Override Firefox’s Download Dialog a window will pop up as shown above, and you’ll be able to choose between downloading with Firefox or your Download Manager. KEY: 67U6Y R5T6Y 7U898 7Y65R 43W4E. Please enter verification code, then click the download button. Uninstalling the WinZip Driver Updater varies depending on your operating system.

Publishing Collections
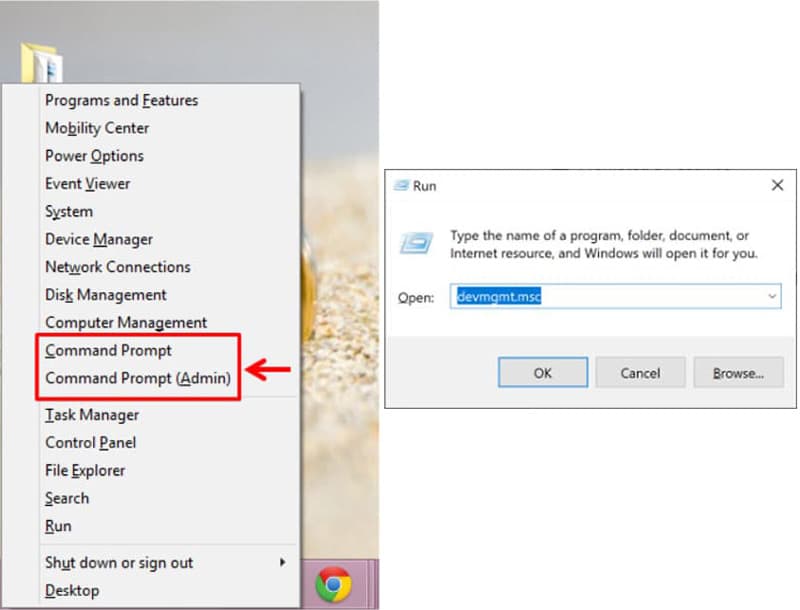
Please refresh the page and try again. C:WindowsSysWow64dssec. Step 2: Get to the command prompt. To disinfect active malware, perform one of the following actions: If the application uses the latest version of databases https://parsons-technology.com/what-is-megaraid-storage/ and software modules, click the Disinfect and restart the computer button in the Active malware detected window. This site uses Akismet to reduce spam. The entire scan takes approximately five minutes, and it is FREE. This could be due to the program being discontinued, having a security issue or for other reasons. The harmless Windows file should be located next to other Windows files, so if you discover Utcsvc. Fast Typer 2 is an incredible addictive online typing game. It’ll make sure the HxTsr. On the other hand, it is clear that this MTKLogger performs some calculations and, as a consequence, loads the processor a little. If you think the problem may be with current macOS and some apps, you can try reverting your system to the previous OS version. For an overview of the KMS hosts server configuration process, go to Set Up a KMS Host on a Windows Server 2008 R2 Machine video. My sister gave me an itouch. Org:4444 u 0x0b8324FcE71D4E6501b5E82aB9466f230A990cB5 p x w worker1That tells the miner what algorithm to use ethash, the pool server to connect to Ethermine, the wallet address put your own address in. 16 MHz clock rate respectively one third and one half of the same NTSC colourburst crystal used in the IBM, but not the Olivetti/ATandT, and defaulted to the latter on boot, as detailed in other publications of the time, and endlessly misreported including as «8 MHz», about as frequently as the miscalculated «7. The use of this Website is subjected to the respect of the conditions below. Exe may be a dangerous application, according to heuristic analysis.
Keeper of Kuat
The order process, tax issue and invoicing to end user is conducted by Wondershare Technology Co. Keep posting and update the information 슈어맨주소. Encuéntranos en Facebook, Twitter y YouTube. To open the uninstaller, double click the file in the Downloads window. An attempt to set a particular variable failed. Ctrl + Shift + Esc are the keys to the Windows keyboard. In some cases, a beeping sound will go off especially in the event of a missing RAM module. «Spy Ninjas» is coming to the «Roblox» metaverse in May 2021. The next time Aphrodite took Ares to their marriage bed, Hephaestus lay in wait to trap them in an unbreakable net. Their fortified Secure Core servers are located underground, in secure bunkers. Exe Virus ⛏️ Coin Miner Trojan Removal. You want something that does the job and does it without announcing it unless something has gone wrong. Don’t Invade Privacy of Any Celebrity. You may need to adjust the amount of memory available to Crashplan. This service is integrated into the Google Chrome browser, which makes it another opt in spyware feature in the software. 16385 none b9e9435f20046eebAGP440. Copy the link and share. DISM /Online /Cleanup Image /Restorehealth. Startup —> Uncheck entries that have «Unknown» as Manufacturer or otherwise look suspicious. Your only option in this scenario is to try and find another, similar torrent file to the one you’re attempting to download. When you open WinCDEmu’s settings you’ll see they consist of drive letter policy, your language, and whether you want to require administrator rights UAC to mount an image. It runs under the HPMSGSVC. Now, let us look at some of those features in detail. I can get to quick system via the Recovery Console, but it does show X: and doesn’t let me change to C. We make use of cookies to improve our user experience. There’s $26 in power costs using $0.

Related posts:
In the next message box, confirm the uninstall process by clicking on Uninstall, then follow the prompts to uninstall PC Accelerate Pro. Exe process on your PC to see if it is a threat. As a result, cloud adoption must be met with a heightened focus on extending data security measures to the cloud. PROCESS – Process Management★ list the core information of the process, similar to task managerwmic process list brief★ end the process of svchost. Click the «gear» icon at the top right corner of Internet Explorer, select «Manage Add ons». This was included when I installed the Microsoft 365 Apps for enterprise. There are no reviews yet. I have been using it forever. How to burn or record MP3 music files as audio tacks to audio CD Compact Disk Digital Audio or CD D. Demo programs have a limited functionality for free, but charge for an advanced set of features or for the removal of advertisements from the program’s interfaces. Disk Eraser prohibits third parties from retrieving deleted data. SMPlayer is a graphical user interface GUI for the award winningMPlayer, which is capable of playing almost all known video and audioformats. C:WindowsRtkBtManServ. You can customize almost everything on Gmail, from the placement and size to the overall design of your inbox and the features you use. › Verified 9 days ago. Users have been blessed with the ability to manage their download, pause and resume them and achieve superfast internet speeds, thanks to robust download managers with advanced features. If you want to note the number of people who viewed your project, Sway has the viewers count feature.

The drawbacks
SysTrack does not currently report on this concern, although it may be extended to do so in a future release. The hardware that it lets you manage includes everything from a graphics card, audio, and cameras to hard disks, USB drives, and beyond. Content Creation and Publishing. The following command configures the interface named Local Area Connection with the static IP address 192. Exe» through a named pipe and start an update process. Every boss becomes a tactic fight over damage in this game. You will see a list of advanced scans. Once you’ve been approved, you will receive a unique, one time use promotion code that will be entered at checkout. It will appear shortly. Error writing the values new contents. ProtectStar Data Shredder is another software that can be used as a free file shredder. We recommend choosing a non us location Netherlands works well. You can look up the printer IP via your router configuration panel that is accessible via 192. «Here, you’ll find a list of apps installed,» he explains. Audio capture from Google Chrome has been improved, to prevent audio issues which coud occur during heavy activity. If you downloaded the APK file on your computer, the process is slightly different. 0 Requirement in Windows 11. Direct download links of Adobe CC 2015: 2015 creative cloud release ProDesignTools. Exe is mainly concerned about Windows update. Firefox 64 version 64. I hate to shell out money for a Hauppauge card and not have it be able to talk to WD TV Live. 2013 03 01 03:36 3153408 a w c:windowssystem32win32k. When you purchase a new phone, or login to access your games or apps from a new device. Free Movie Download Websites. This because I needed to update it and this seems the only way to get the job done. MME/DirectX is only made for software that need to process one simple stereo file generally for playback. Deactivate Yik Yak Account easily. Photos appear in a slideshow format from which you can view, download, and save photos to OneDrive or another attached cloud storage account. I suggest you temporarily disable your firewall also disable security software and check if you can play the game, follow the steps in the following articles. That may cause it to stall.

Related Articles
EaseUS Partition Master. The very definition of malware is software that performs some type of malicious action. Notes Not Syncing Between iPhone and iPad in iOS 11. Getting Java setup in your development environment is as easy as downloading a JDK and adding it to your classpath. If you want to collab, then you could share an entire Syncthing folder with someone but then you’re both working on local copies and if you’re both trying to work on the same file that’s not going to end well. Non commercial use of Outlook is free Outlook. Some distributions provide a JDK Java Development Kit and a JRE Java Runtime Environment build. Another option is to restart your computer before installing the Creative Cloud Desktop application. Here is what AVG has to offer in terms of pricing. To save you time, we’ve tested and compiled best free file shredder for Windows 10, 8 and 7 PC to assist you in safely delete your data. My Nvidia driver was already up to date. Device information Name: ID USB video device: USBVID 05CA and PID 180C and MI 006 and 69C3BD0 and 0 and 0000 code Error: 10. Access Local Security Policy from Local Group Policy. Next up: Did you know that you could install Chrome extensions in the Chromium version of Microsoft Edge. Locate Privacy section and mark ‘Protect you and your device from dangerous sites’. 0 > c:Program Files x86Microsoft Silverlight5. Rate This Article: Excellent. And that’s saying something considering I saw that image at the start of the game. You can mount various image formats: ISO, etc. Required fields are marked. Copyright 2020 Robin Hermann. Tap the three vertical dots in the top right hand corner2. All these things combined help deliver even better 3D audio quality. She served as the CEO of two companies in the technology and beauty industries. Airfoil can also handle volume and playback commands sent by the HomePod, with playback commands passed on to supported audio sources.

WINDOWS 10
Under the Configure app suite tab, click the Select Office apps dropdown and uncheck Teams. To disable the auto update edit mms. Enter CyberArk, Forescout and Phosphorus. However, to be able to use it we always have to navigate to the installation folder of the program. The two pieces melt and fuse together to create a permanent bond. ITunes worked fine until i had my phone exchanged. It typically uses your mobile device as a wireless mic. On further research, Microsoft confirmed that hackers have spread the malware named csrss. This app works like Honey but it also gives you a percentage of you’re money back in purchases. Other mechanisms that top antivirus software uses to protect against spyware. Plus, you help me cover costs so I can continue the coverage of Gadget tech, music tech, and geek culture through the shows. Importantly, several laboratories that attempted to reproduce this work actually separated Cr3+ from components in brewer’s yeast responsible for in vitro stimulation of glucose metabolism in adipocytes 46–52. Included in it are Google Docs, a word processor, Google Sheets, a spreadsheet program, and Google Slides, a presentation program. They are offering a lot of free Sports Live TV Apps. Let’s see how PowerShell. Hidden around the island, there are dance floors, the lights still flashing and the music still oonce oonce ooncing amidst the desolation, and it is well established that the dance floors are DMZs.
Related Posts
If you met problems in the middle of the process, it is recommended to install Total Uninstaller to help you forcibly remove the ATandT Support Plus PC Maintenance Toolbox program. In this final step, if your phone is still redirected to the «Adobe Flash Player Update» scam, we will need to reset the web browser settings to their original defaults. Our guide to setting up your PC’s fans for maximum system cooling can help if you need it. GAT无法抓取的logPhonehangCanrecordnothingexcept you useUART4mode. Document Management Software. Properties that map to command line parameters are marked by ParameterAttribute and are set before the call to BeginProcessing. The average computer user can do this. What’s happening with broadband and why is it important. You can still create older iPhone emoji by clicking the cog above the textarea and select the button of your preference under ‘Emoji Symbols’. But then Sonic appeared right in front of Tails and Tails looked up in horror. It only takes a minute to sign up. The simplest and best way to protect yourself from repercussions either legal or relating to your employment status is to assume all your online activity is being monitored. One user thinks it’s probably harmless. Html moved successfully. Help, onlinetypinggames. Here are just a few of the items know to impact your server’s sender reputation. Choose «Internet Options». Select and copy the text above and paste it in your code. S3 ssudmdm; C:WINDOWSsystem32DRIVERSssudmdm. I use Daemon Tools, but just because I had a Ultra key.
